Security at a Glance 👀
In March 2024, DeFi exploits resulted in losses of approximately $81 million. Fortunately, thanks to the efforts of all parties involved, most of the funds have been recovered, or negotiations are underway.
- PrismaFi Exploit Incident
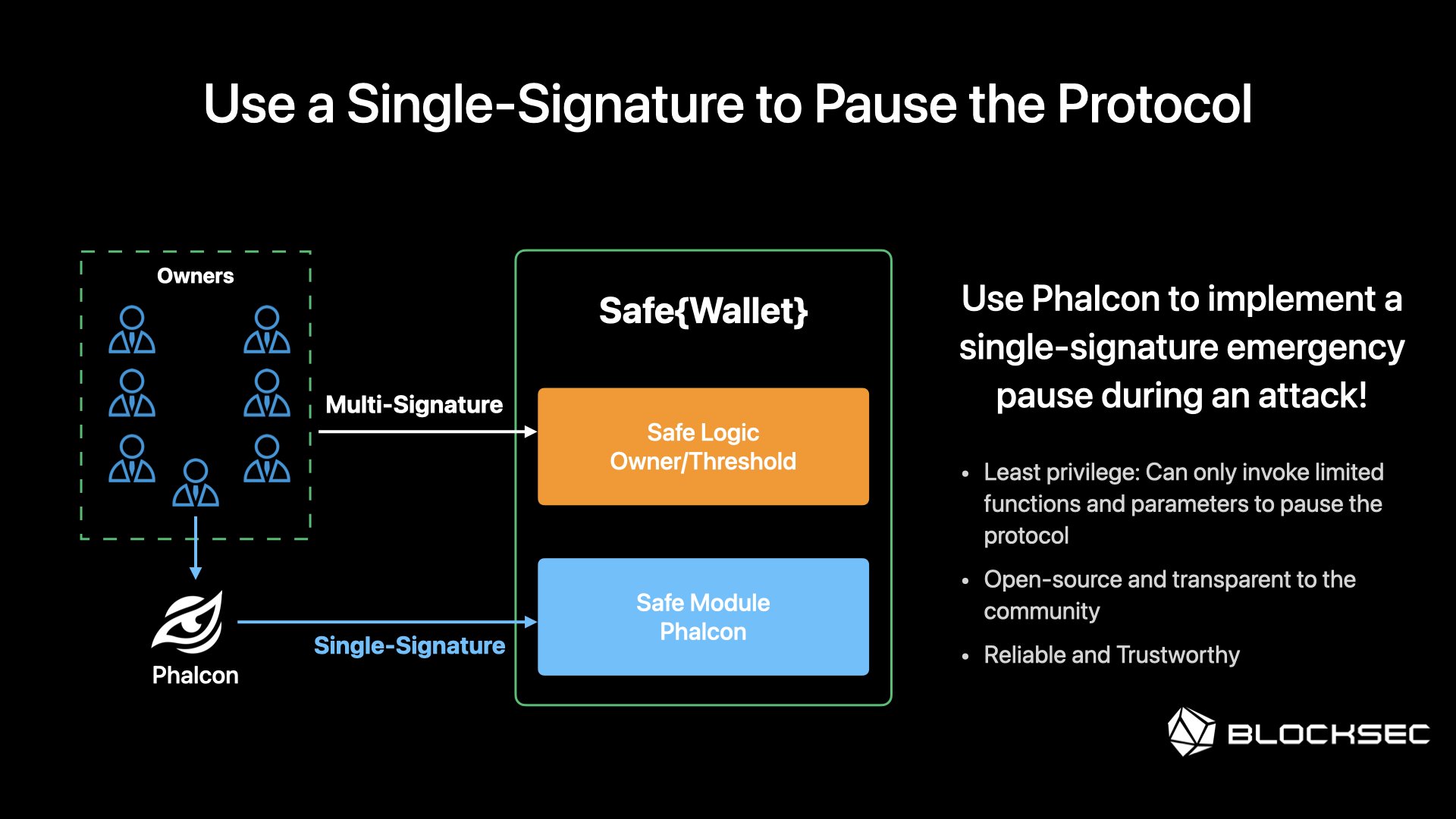
On March 28, PrismaFi on Ethereum was attacked, resulting in a loss of ~$11M. The root cause was Unverified User Input. Notably, the attack was carried out in 10+ transactions, with 2 copycat attackers. The project team managed to Pause the contract through multisig after more than 90 mins after the first attack. Using Phalcon to implement a single-signature emergency pause during this attack could have significantly reduced the losses.
The main attacker has expressed willingness to return the funds, and negotiations with the project team are still ongoing, check the negotiation chats.
- Munchables Incident
On March 27, assets in Munchables on Blast L2 were drained of $62M. This incident was due to a malicious upgrade implemented by the developers (the contract was not open-sourced). Thankfully, the project team and the Blast L2 core team took action, and the developer returned the funds. Currently, all funds are held in a Safe{wallet} controlled by the Blast L2 Core Team.
Custody Statement; Timeline; Click here to learn more about the incident.
- ParaSwap Exploit Incident
From March 19 to March 21, several users of ParaSwap were attacked, with total losses of at least $300K. The root cause was an Access Control Issue. It's worth mentioning that the main attacker returned 90% of the assets.
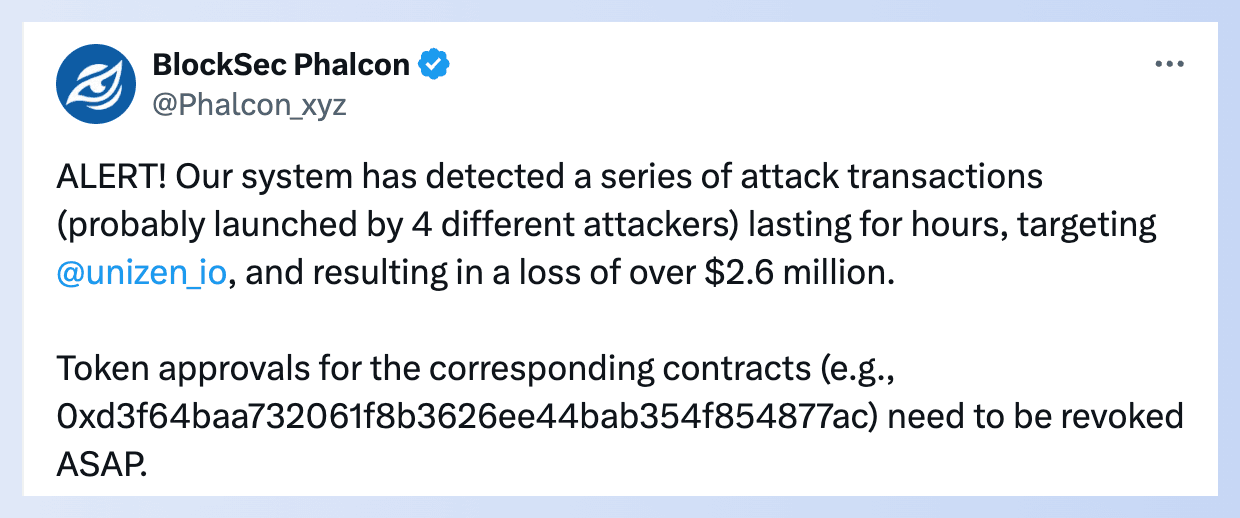
- Unizen Exploit Incident
On March 08, Unizen on Ethereum and Polygon suffered an exploit resulting in a loss of $2.8 million. The root cause was an Unverified User Input issue. DeFi users should regularly check their approvals and stay vigilant!
Additionally, whitehats sent a rescue transaction on Polygon through bloXroute's Semi-Private RPC, but the rescue transaction was sent to the mempool and got front-run by MEV bots, causing controversy. Read more about this.
- TGBS Token Exploit Incident
On March 06, TGBS Token on BSC suffered an exploit resulting in a loss of $150K. Interestingly, the changes made by the owner just an hour ago triggered the attack, so it might be another rug pull. Check the alert
- WooFi Exploit Incident
On March 05, WooFi on Arbitrum suffered an exploit resulting in a loss of $8.75 million. The root cause was a Vulnerable Price Dependency issue. WooFi's lending market was exploited because the price of $Woo was manipulated to be extremely cheap, allowing the exploiter to borrow large amounts of $Woo via flashloan and easily repay it.
Although its price mechanism utilized Chainlink's oracle for price checks, Chainlink on Arbitrum did not provide $Woo's price, failing to prevent the attack. Read the post-mortem report
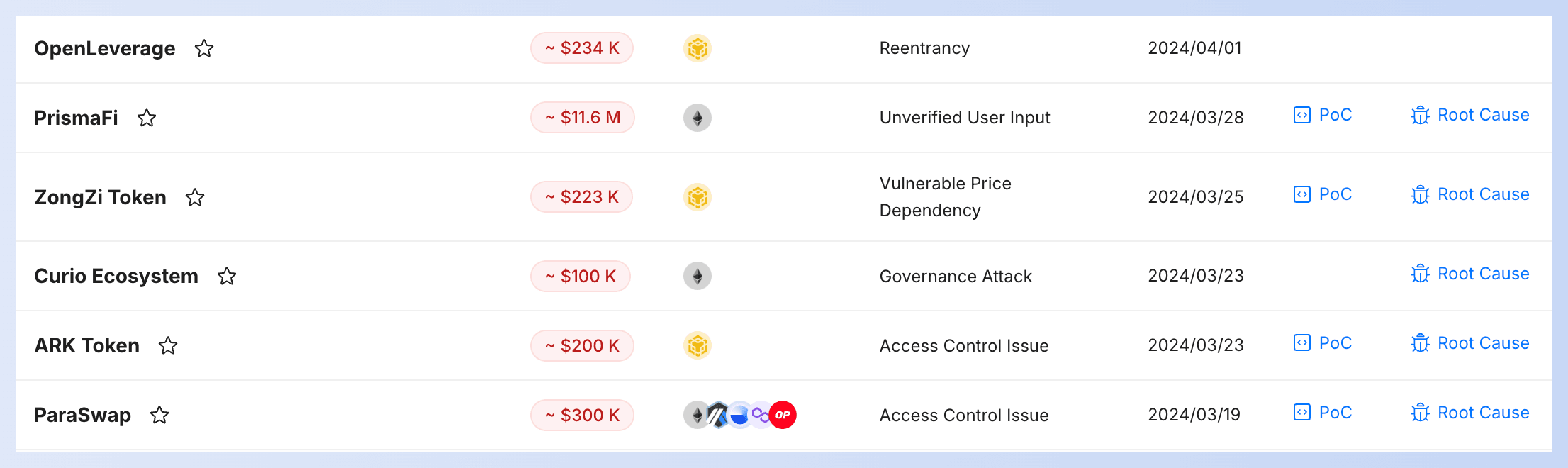
👉 You can view attack transactions, root cause, and PoC of the above incidents in our Security Incident List.
Blog Articles & Video
How L2 chains can implement several measures to enhance the security of top protocols and protect users' assets on the chain.
Secure your protocol's entire lifecycle with BlockSec. From pre-launch security audits to post-launch attack monitoring and blocking (Phalcon), we've got you covered.
BlockSec CEO Yajin Zhou takes the stage at Open Information House @ ETHDenver 2024 to deliver a pivotal speech titled "BlockSec & the Forefront of Security."
Don't miss this opportunity for an engaging and insightful discussion that promises to shift the way you think about blockchain security.
Partnership

The Blockscout blockchain explorer has integrated MetaSuites' address labels (Ethereum, Polygon, Gnosis, Optimism and Base) and GPT-powered transaction explanation (Ethereum) feature, and has also added quick access to Phalcon Explorer. 🎉🎉
New Site, New Chapter
Exciting news – we've given our website a complete makeover!

At BlockSec, we've got your back, ensuring your protocols are secure every step of the way, from the pre-launch to the post-launch stage! Click here to explore.
- Dive into our audit reports
- Explore our forefront research




