Security at a Glance 👀
In February 2024, DeFi exploits have led to losses of around $8 million. Numerous malicious proposals have been detected, signaling a cautionary note for DAOs. Additionally, a backdoor found in Tornado Cash's frontend allowed a bad actor to steal more than 3200 Ether.
DeFi Exploits
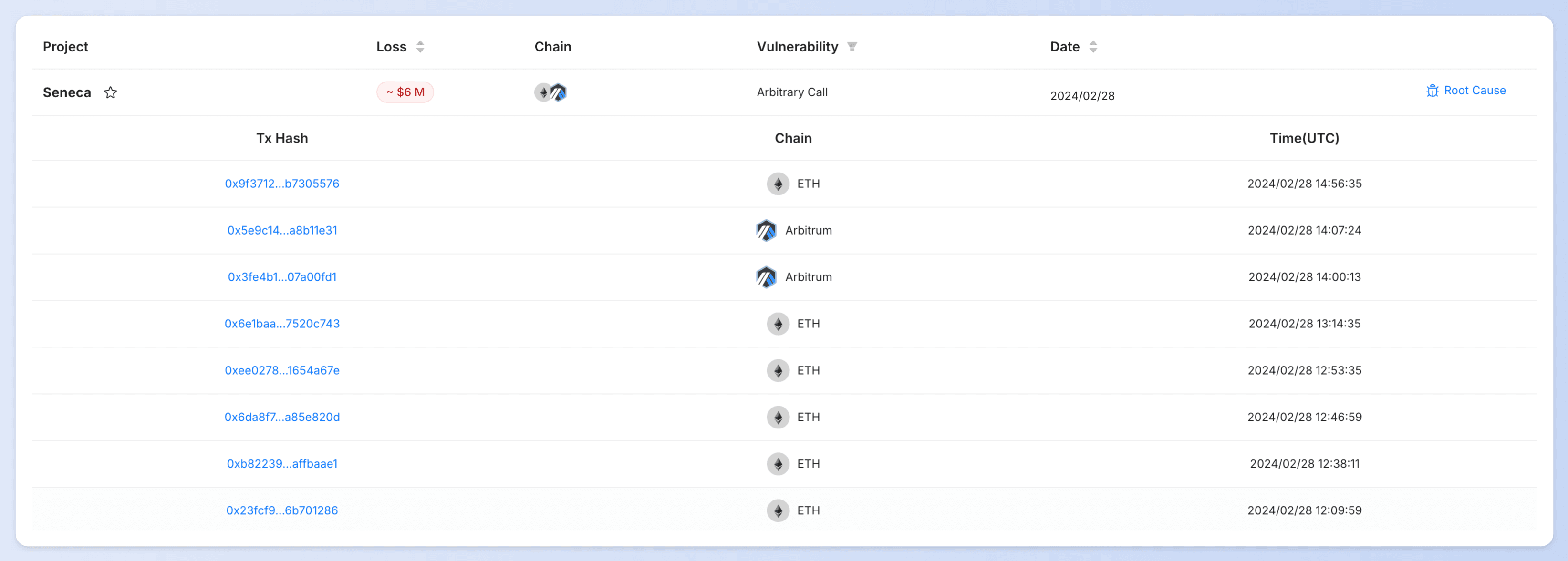
- Seneca Exploit Incident
On February 29, Seneca on Ethereum and Arbitrum suffered an exploit resulting in a loss of $6 million. The root cause was an arbitrary call issue. DeFi users should regularly check their approvals and stay vigilant! Read more about this.
- Blueberry Exploit Incident
On February 23, Blueberry on Ethereum suffered an exploit resulting in a loss of $1.4 million. The root cause was the use of inconsistent logic for token price normalization, involving a mismatch between the price sources and their respective normalization methods. The coffeebabe_eth's MEV bot successfully front-ran the exploit and returned 367 Ether. Read more about this.
- DeezNutz_404 Exploit Incident
On February 22, DeezNutz_404 on Ethereum was exploited, with total losses estimated at around $170K. The root cause was a calculation issue caused by self-transfer. The ERC404 series of tokens have experienced multiple similar exploits. Please exercise caution when engaging in investments. Read more about this.
- Particle Trade Exploit Incident
On February 15, Particle Trade on Ethereum was exploited, resulting in approximately $140K in losses. The root cause was unverified user input. Read more about this.
- CheckDot Protocol Malicious Proposal Incident
On February 1, a bad actor submitted a malicious proposal to Checkdot Protocol, with potential losses of $120K. After we informed the Checkdot team, they acknowledged the severity of the threat as critical and implemented a fix.
We thwarted a sneaky attack on @Checkdot_proto and kept users' assets safe. The team acknowledged the severity of the threat as critical and has implemented a fix.
— BlockSec Phalcon (@Phalcon_xyz) February 4, 2024
Here's a breakdown of the incident.
🚨 We have detected multiple malicious proposals (nounsbr, LeagueDAO, wearecultdao etc. ) in February and would like to remind DAOs to be aware of the risk of proposal attacks.
👉 You can view attack transactions, root cause, and PoC of the above incidents in our Security Incidents List.
Backdoor
- Tornado Cash Frontend Backdoor Incident
A malicious developer implanted a backdoor in the frontend of Tornado Cash, stealing depositor's credentials and at least 3200 Ether in deposits. After Tornado Cash was sanctioned, the project transitioned to community governance. Since then, the project has been subjected to multiple proposal attacks.
Blog Articles
Top Ten "Awesome" Security Incidents in 2023
"What we learn from history is that we do not learn from history."

In this blog, we outline the top ten security incidents worth mentioning in 2023 and their reasons.
For each security incident, we also present the root cause and the attack steps in the following separate blog posts.
-
#1: Harvesting MEV Bots by Exploiting Vulnerabilities in Flashbots Relay
-
#3: KyberSwap Incident: Masterful Exploitation of Rounding Errors with Exceedingly Subtle Calculations
-
#4: Curve Incident: Compiler Error Produces Faulty Bytecode from Innocent Source Code
-
#5: Platypus Finance: Surviving Three Attacks with a Stroke of Luck
-
#7: ParaSpace Incident: A Race Against Time to Thwart the Industry's Most Critical Attack Yet
-
#8: SushiSwap Incident: A Clumsy Rescue Attempt Leads to a Series of Copycat Attacks
-
#9: MEV Bot 0xd61492: From Predator to Prey in an Ingenious Exploit
-
#10: ThirdWeb Incident: Incompatibility Between Trusted Modules Exposes Vulnerability
Demystify the Access Control Mechanism in Puffer Protocol
Curious about how #PufferProtocol keeps its funds secure? Check out BlockSec's deep dive into its access control architecture! Understand the roles, smart contracts, and strategies for managing over $900M assets. Knowledge is power!
BlockSec’s Perspectives and Solutions on the Security of L2 Blockchains
In this blog, we will first systematically review the security challenges of L2 blockchains and then propose our solutions.
Podcast: How BlockSec Intercepted $15M of Web3 Exploits in Real Time
Andy Zhou, our CEO, joined the host DeGatchi on the Scraping Bits podcast to talk about how we block attacks in Web3. This blog is a transcript of the podcast content.
Exciting Partnership
We are excited to announce our collaboration with Puffer Finance (one of the top restaking protocols, with a TVL of $461M) for a comprehensive audit of the campaign.
Moreover, we are integrating Phalcon (our attack monitoring and blocking platform) into Puffer’s protocol to enhance their security measures.

Events
Mar 1-9, the BlockSec team embarks on our US trip.
We're open for collabs, chats, and all things blockchain. DM us for meetups!
📍 First stop: #ETHDenver, Mar 1 to Mar 2
📍 Second stop: Silicon Valley, Mar 3 to Mar 9
Product Updates
In February, we hosted the Phalcon 3.0 Webinar and collected valuable feedback about Phalcon from users.

In March, we are going to launch Phalcon 3.0—a next-gen SaaS platform that auto-detects and blocks hacks, tailored for protocols, LPs/traders, L1/L2 chains, and exchanges.
Brace yourselves for a Web3 security revolution! 🚀
Stay informed, stay secure! See you next time! 👋




