Why Security is Important for L2
Security is crucial for Layer 2 (L2) blockchains as they gain popularity. With advancements like the Dencun upgrade, gas prices on L2 are decreasing, making them more attractive. Additionally, the introduction of BTC L2 enhances liquidity in the L2 ecosystem, attracting more users.
Unlike Layer 1 (L1) blockchains that serve as a foundational infrastructure for various decentralized applications (Dapps), L2 chains typically focus on a specific type of application, creating a dedicated ecosystem. Therefore, operators of L2 blockchains need to prioritize the security of top Dapps in their ecosystem, as these applications often hold the majority of the Total Value Locked (TVL) on the chain. An attack on these top apps could lead to a collapse of the chain's ecosystem, as users' assets are concentrated in these applications.
Munchables Incidents
An example of the importance of security in L2 is the Munchables security incident on the Blast chain. On March 21 (UTC), a malicious contract was updated, and five days later, on March 26 (UTC), an attacker exploited the upgraded contract to steal around 62 million USD. The total assets at risk were 97 million USD, nearly 4% of the total TVL on the Blast chain. Fortunately, in this case, the attacker returned all the assets, resulting in a happy ending. However, it's important to note that relying on the attacker's goodwill is not a sustainable security strategy.
How L2 Operators Can Do Better
Layer 2 (L2) chains can implement several measures to enhance the security of top protocols and protect users' assets on the chain. Here are some suggestions from our perspective:
-
Establish a Security DAO: A decentralized autonomous organization (DAO) focused on security should be created to involve reputable security companies and community researchers. This would facilitate communication between the chain, decentralized applications (DApps), and the security community, helping protocols find trusted security providers and handle security incidents professionally.
-
Active Attack Monitoring and Automated Responses: Chain operators and the user community should actively monitor for potential hacks and have mechanisms in place to take automatic actions. For example, in the Munchables incident, there was a five-day window before the actual hack occurred. If the chain operator or the Munchables protocol had adopted a solution like BlockSec Phalcon (or similar), the hack could have been prevented.
-
Develop User-Friendly Security Tools: More intuitive security tools should be developed to help the community quickly understand the root cause of a security incident and take appropriate action. These tools could include transaction virtualization tools to understand complex transactions and fund flow tracking tools to trace the hacker's fund movements. By taking a proactive and responsible approach to security, L2 chain operators can enhance the overall security of their ecosystems and better protect the top protocols and users' assets on the chain.
BlockSec’s Solution
BlockSec, as a comprehensive security provider, offers various security services and tools to ensure the safety of protocols before and after deployment. These tools and services are widely utilized by the security community to analyze security incidents and trace stolen funds.
BlockSec Phalcon
Phalcon is a platform designed for monitoring hacks and automatically taking actions to block them. With Phalcon, users can receive early security intelligence and automate their responses to hacks. The system features flexible rules and templates for easy configuration, assisting Layer 2 (L2) chains in maintaining vigilance over the security of top protocols and fostering a thriving ecosystem. BlockSec is collaborating with leading L2 chains like Manta and Merlin to bolster the security of their ecosystems.
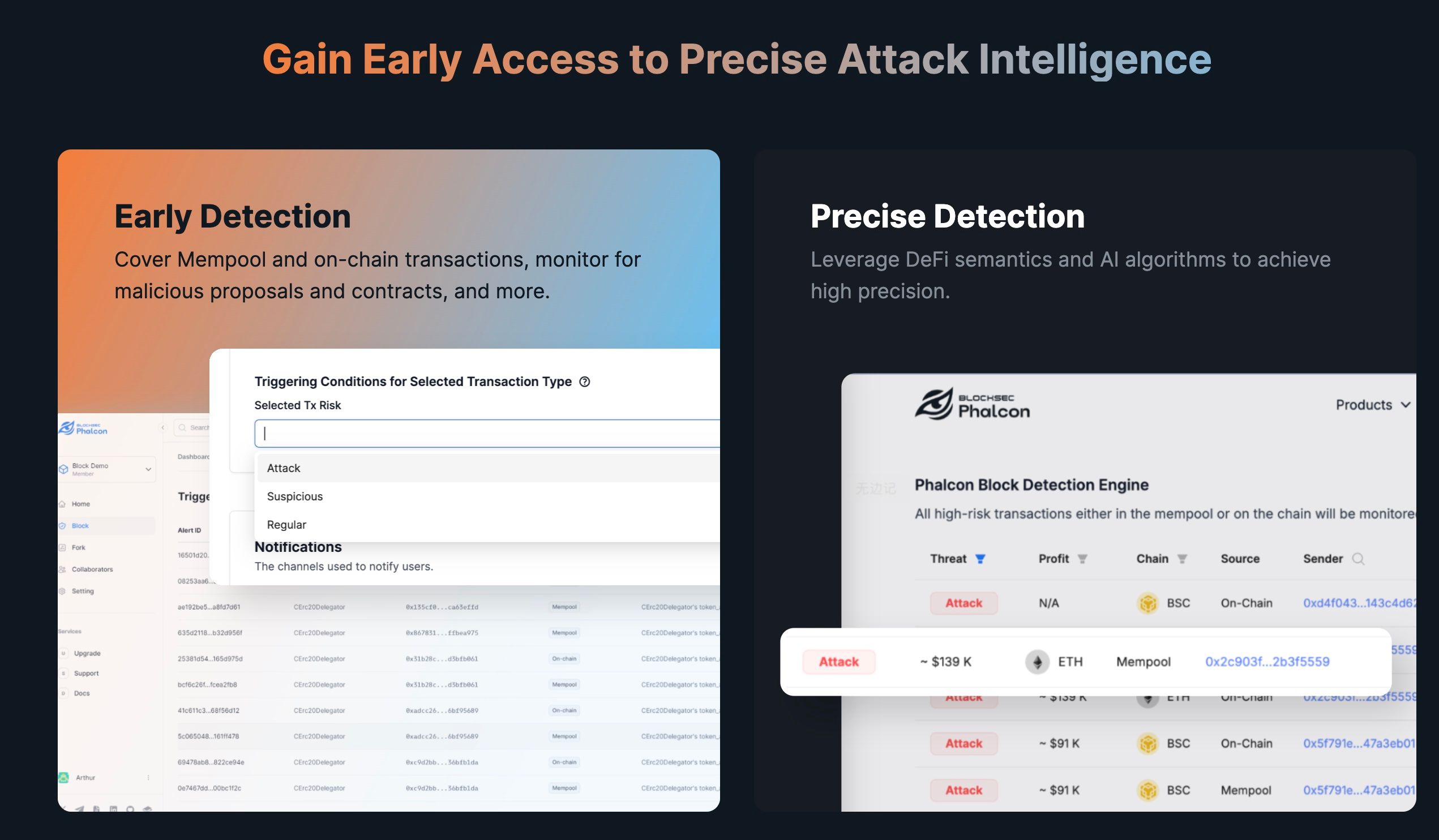
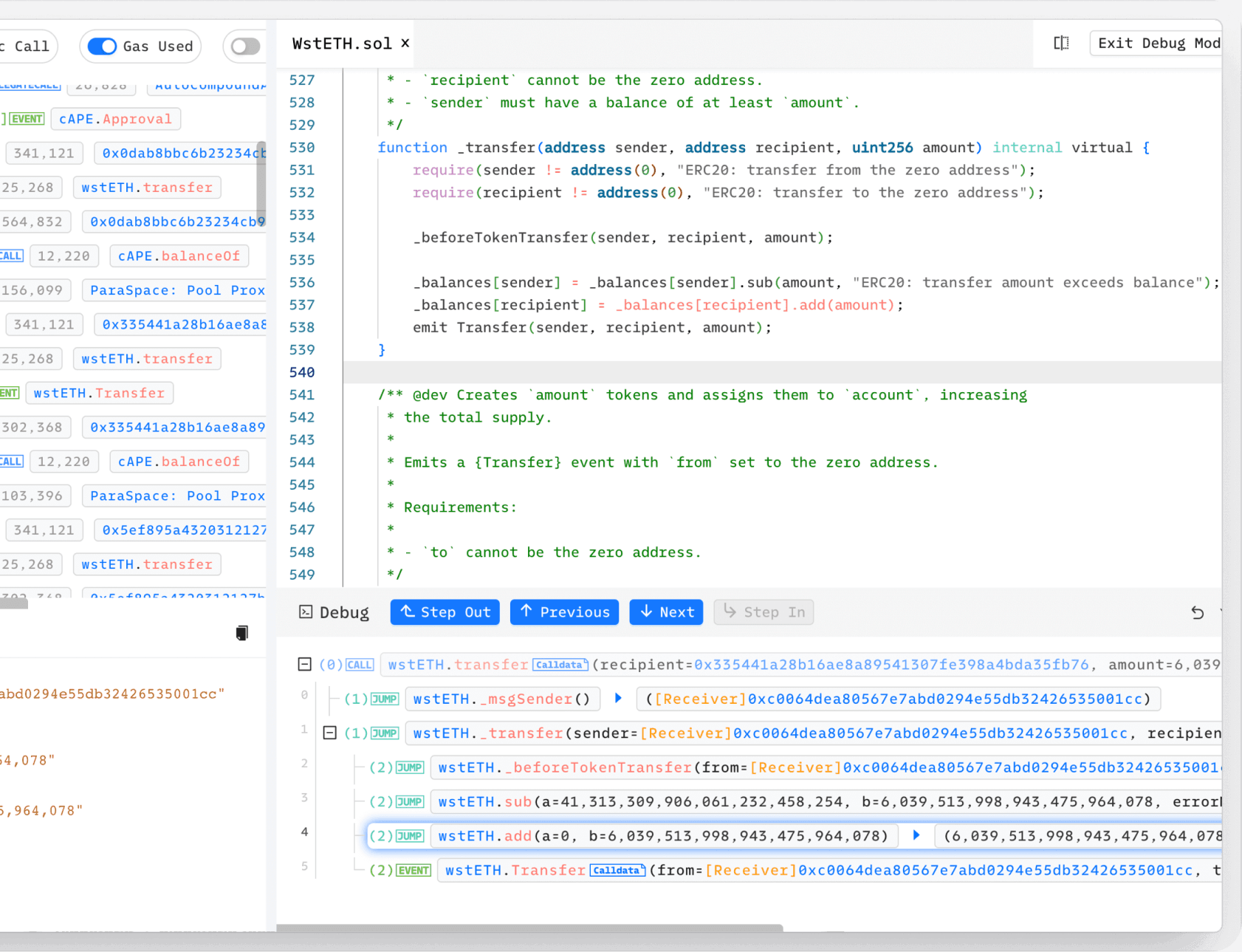
Phalcon Explorer
Phalcon Explorer is a transaction virtualization tool that provides detailed information about a transaction, including the invocation flow, storage changes, and transaction simulation. This tool is instrumental in analyzing hacks to understand their root causes. It has become a widely used tool in the security community and is considered the standard for security analysis.
MetaSleuth
MetaSleuth is a cryptocurrency tracking and investigation platform that traces fund flows between different addresses. Its intelligent analysis and ability to track cross-chain transactions make it an essential tool for conducting investigations.
Action Now to Protect Users Assets
If you are an operator of an L2 blockchain, contact us (contact@blocksec.com) to deploy BlockSec's tools into your chain to enhance the security of your ecosystem, attract more user assets, and protect them effectively.




