We found a new type of phishing method that is becoming popular. Instead of deploying phishing contracts (security vendors could label that), the scammers are abusing some legitimate contracts to perform the attack.
In this blog, we will show you the way scammers use and provide suggestions for how to avoid being phished.
Overview
Usually, scammers deploy phishing contracts to steal tokens from victims. Specifically, their phishing contracts contain suspicious payable and multi-call functions. Users visiting phishing websites will send ETH or approve tokens to these contracts. However, security vendors and wallets could detect and flag these phishing contracts, leading to a prohibition of transactions directed toward them.
However, we discover that scammers abuse legitimate contracts deployed by reputable Web3 projects for their phishing purposes. And these legitimate contracts cannot be labeled as phishing and blocked. We name it "ROP" in Web3 phishing websites since they DO NOT deploy new contracts but reuse existing and legitimate contracts for phishing. This is similar to the ROP attack (or code reuse attack) in traditional software security areas.
Specifically, Return-oriented programming (ROP) is a computer security exploit technique that allows an attacker to utilize code snippets in existing libraries. In Web3 phishing, "ROP" refers to leveraging contracts deployed by legitimate projects for fraudulent purposes. This phenomenon was first reported by the Twitter account @MevRefund in a post.
How Traditional Web3 Phishing Contracts Work
In the early phases of Web3 Phishing, scammers will set up an Externally Owned Account (EOA) and lure users to transfer ETH or approve other tokens to this account. However, this behavior is now easily detected by wallets and discovered by users. As a result, scammers have turned to deploying phishing contracts. For ETH phishing, scammers typically employ a payable function with suspicious names such as 'Claim' or 'Security Update.' These enticing function names prompt users to sign phishing transactions and transfer ETH.
For ERC20 and ERC721 token phishing, scammers will lure users into approving their tokens to the phishing contract. Subsequently, the Multicall function in phishing contracts will be invoked to transfer users' tokens. In particular, the Multicall function is designed to execute multiple specific internal transactions in a single call. Different phishing schemes, e.g., NFT Zero-order purchase, ERC20 approval phishing, or ERC20 permit phishing, use different phishing transactions. This enables them to configure the transaction parameter and leverage Multicall to launch specific phishing transactions based on the corresponding phishing schemes.
Now, many popular Web3 wallets have built their phishing account blacklists. They actively inform users and prevent transactions directed towards these fraudulent accounts.
"ROP" in Web3 Phishing
To circumvent the phishing account blacklist mechanisms, scammers turn to some accounts that cannot be added to the blacklist. Specifically, they abuse Multicall contracts deployed by legitimate projects, leveraging their functionality for executing complex transactions. Given that these legitimate contracts cannot be labeled as phishing accounts, scammers prompt users to approve tokens to these contracts. Since these legitimate contracts can be invoked by anyone (no access control), scammers can immediately abuse them to transfer users' tokens. The following figure shows the whole process.
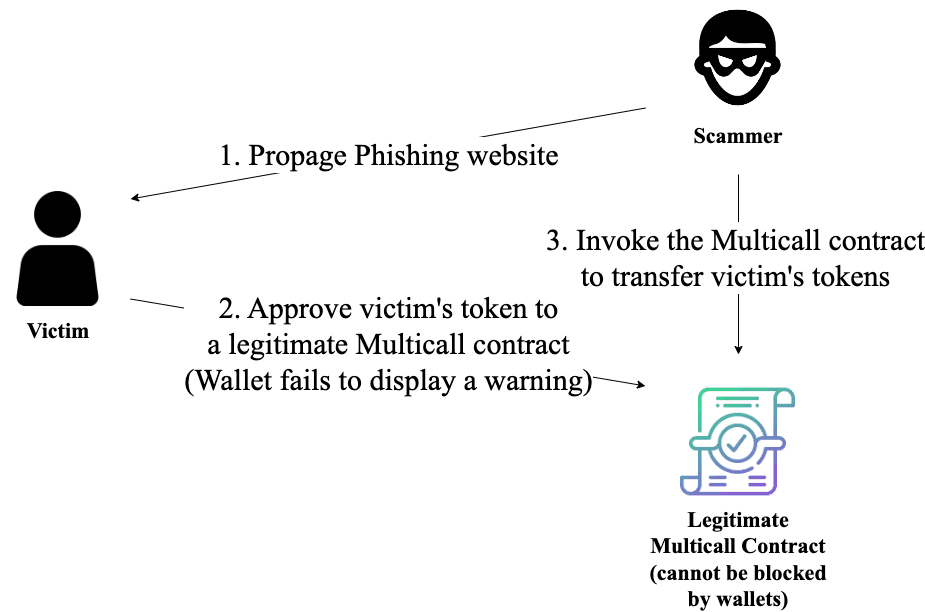
For example, Angel Drainer, a well-known phishing criminal syndicate, has leveraged Uniswap V3: Multicall 2 to launch 89 phishing transactions. Note that the legitimate multi-call contract was intended not to hold any assets. So, it's fine to be invoked by anyone in its design. However, the scammer abused this contract to perform the phishing attack without deploying their phishing contracts.
Suggestions
We encourage users to be cautious and carefully scrutinize transaction details before proceeding with any actions, espeically the approve trasnactions. Always check your approval and revoke any of suspicious ones.




